Maybe you should worry more about your neighbours…
by Vic Harkness, Security Consultant at F-Secure
Hacking cars is a very sexy subject; the movie ‘Fast & Furious 8’ showed us how compromised vehicles could hypothetically be used to cause chaos and disruption. Whilst most people can understand that the scene was a dramatisation of how cars can be hacked, it’s based in a real problem. Although cars can’t completely drive themselves yet, we’re rapidly approaching that point. Perhaps in 10 years vehicles will be entirely autonomous. If we don’t secure our future vehicles, then bad people with way too many computer screens will be able to control them.
To assist car manufacturers in reaching higher levels of vehicle autonomy, various EU bodies have released documents describing how future Connected/Autonomous Vehicles (CAVs) should communicate with each other. These proposals also detail future intelligent roadways which will be able to share useful information with the vehicles which drive upon them. F-Secure conducted a study examining the security of these high-level proposals to assess where the security gaps are likely to lie.
We identified numerous potential vulnerabilities in these future systems, concentrating on flaws in the ways in which vehicles will communicate. And, based upon the current proposals, the future visions of highly interconnected vehicles are not viable. Attackers will be presented with near endless opportunities to deny vehicles access to the network, meaning the cars would be forced to make decisions on their own. As such, one of the key recommendations of the study is that all future vehicles should be able to operate safely, even if they lose access to overarching data sharing mechanisms.
To look at future threats to CAV infrastructure, or any network, we need to assess what type of attacker is likely to be targeting it. In general terms, threat actors seen in cyber space can be described using this pyramid: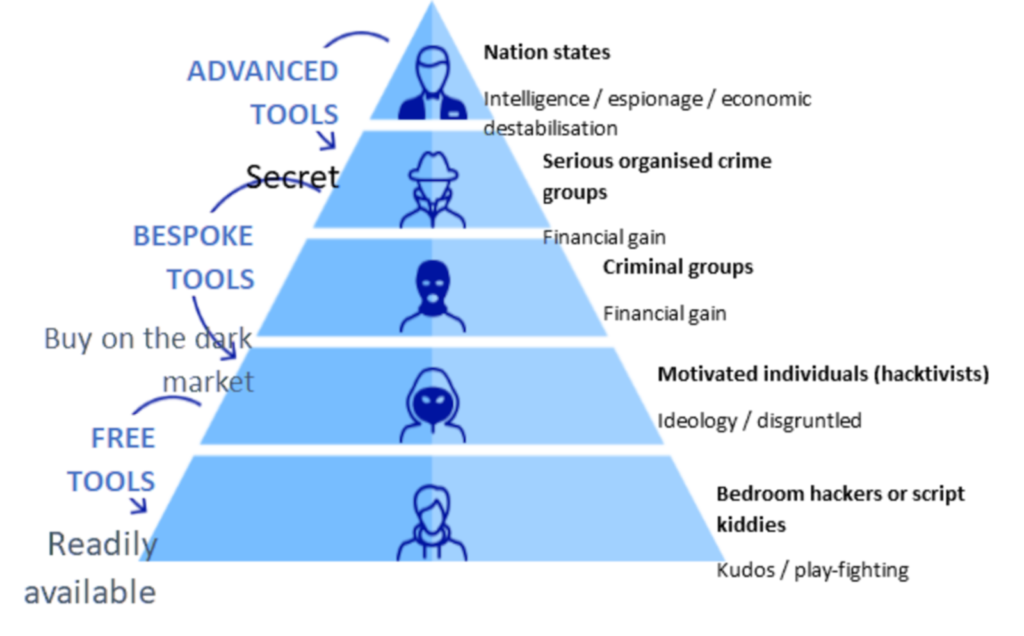
At the higher levels of the pyramid, we have the big scary groups seen in Fast & Furious 8. Thankfully, there are very few of these groups. They tend to be very well-resourced, as they are backed by nation states or even high-level crime organisations with access to top-tier hackers who can create highly bespoke tooling and attacks.
Moving down the pyramid, the numbers become greater, but the resource levels lessen. The most common type of hacker, known colloquially as the script kiddie, is generally not very well resourced. Our script kiddie has probably heard about the Low Orbit Ion Cannon online and might try to run it against his school’s website. On the one hand, he doesn’t really understand what he’s doing. On the other, he is one of thousands. An attacker only needs to get lucky once, but the defender needs to successfully fend off thousands of attacks.
For the study, F-Secure examined the types of goals that these varying levels of threat actors may have, and how these goals could be aligned with their skillsets. This knowledge was combined with the results of our security review to create hypothetical attack paths which an attacker could use to gain access to the future CAV networks and reach their goals.
As an example, I would like to introduce my favourite neighbourhood threat actor: Bob the Grumpy Guy.
Bob lives in a small village, which has a section of smart roadway running through it. He is upset by the speed at which the cars travel through the village and wants to slow them down. He has read online that the roadside units (RSUs) placed every 500m along the roadside control the speed at which cars drive, and so he decides to target them.
Bob spends some time learning about hardware security online. One night he takes his laptop and a crowbar to an RSU, which is hidden behind some trees. The RSU is in a locked cabinet, but Bob manages to lever it open with the crowbar. The physical tamper detection system of the RSU detects the unexpected opening of the door and sounds an alarm. An alert is sent to the CAV network requesting investigation. The loud alarm startles Bob, and he returns home.
Based on his experience with the RSU, Bob decides to try and use other devices to get to the RSU. His neighbour has a new intelligent vehicle, which connects to the RSUs. Bob does some research on his neighbour’s new car, and discovers the car broadcasts a hotspot which drivers can connect their phones to. Bob reads a web forum and finds unofficial reports saying the technology used for this hotspot has an abusable authentication vulnerability.
As Bob is within the hotspot’s range, he can exploit the vulnerability to connect to the car from his bedroom. Using his knowledge of network security, he can pivot through the car’s internal networks until he finds the service which allows it to interface with the RSU. After some trial and error, he learns how to send status update messages to the nearby RSU. Bob uses these to send the RSU many reports that the road is covered in black ice. The RSU collates these reports and does not correctly identify that they have all come from a single vehicle. The RSU updates its model with the presence of black ice and decides that the speed limit for that area should be lowered.
The dynamically updated road signs along the village now display half the previous speed limit. Autonomous vehicles automatically adhere to them, as do most manually driven cars. Bob is happy once again.
Bob’s attack path can be described as thus: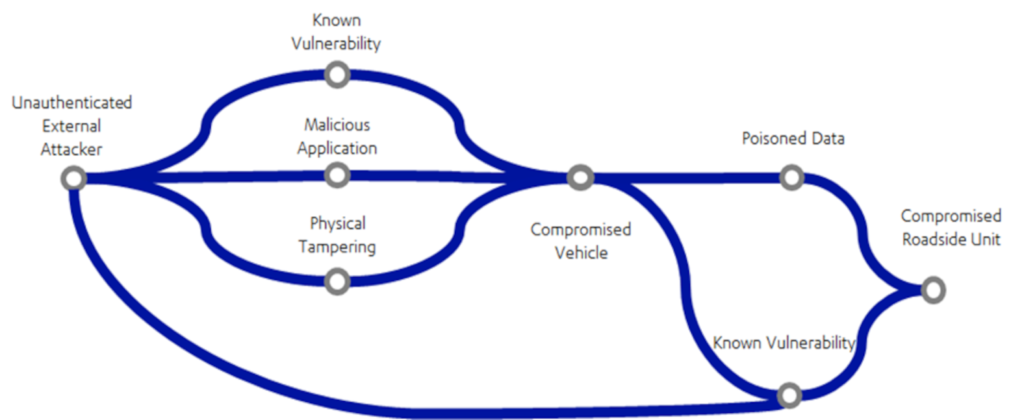
Based on this diagram, we can we see numerous opportunities to stop Bob. If only the vehicle didn’t have unpatched vulnerabilities. If only the RSU didn’t trust data coming from the vehicle.
Scenes like the ones in movies do not come from a single point of failure. They come from multiple system weaknesses being stacked together until a full chain compromise is reached.
Fortunately, there is still time to anticipate these weaknesses and prevent their exploitation by Bob and threat actors of all kinds. Beyond our recommendation that representative CAV testbeds be created to test for, and address, the vulnerabilities we identified prior to any safety-critical deployments, we identified an immediate need for overarching guidance on CAV and ITS security.
A consortium should be formed that includes government, vendors, and the security industry. This group would aim to establish and maintain ITS security standards that would need to meet before any device is deployed on the intelligent roadway infrastructure. Likewise, security consultancies would need to be accredited before providing auditing services.
Finally, the need for thorough detection and logging capabilities within ITS networks is of extremely high importance. Whilst solid security standards will help to prevent lower-grade attackers from compromising the networks, it is inevitable that a breach by a high-grade threat actor will occur at some point. Complex automated detection and logging will help to identify when such a breach has occurred, so that remedial actions quickly to keep the roads safe and open.
For more information, please read our full report here